Configure Cisco ASA NAT Port Forwarding
NAT (Network Address Translation) Port Forwarding is a feature of NAT that allows incoming traffic to be forwarded to a specific device or service on a private network based on the port number of the incoming traffic. This can be useful in scenarios where a device or service on a private network needs to be accessible from the Internet, but the device or service does not have a publicly accessible IP address.
Here is an example topology that illustrates how NAT Port Forwarding might be used in a network:
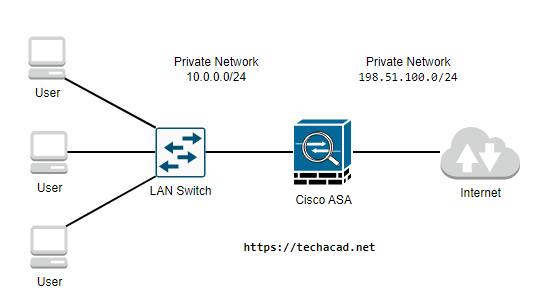
In this topology, the Cisco ASA is connected to the Internet and to a private network. The NAT pool is used to translate the private IP addresses of devices or services on the private network to publicly accessible IP addresses. When incoming traffic from the Internet is received on the Cisco ASA, it is forwarded to the appropriate device or service on the private network based on the port number specified in the NAT rule. The security rule allows the forwarded traffic to reach the destination device or service on the private network.
To configure NAT Port Forwarding on a Cisco ASA, follow these steps:
- Define the NAT pool that will be used for NAT Port Forwarding. This pool should contain a range of publicly accessible IP addresses that will be used to translate the private IP addresses of the devices or services on the private network. For example:
object network NAT-POOL
subnet 10.0.0.0 255.255.255.0
range 10.0.0.1 10.0.0.254
- Define a NAT rule that will apply NAT Port Forwarding to the traffic from the Internet. This rule should specify the NAT pool defined in step 1 as the source of the translated addresses, and should specify the traffic to be forwarded based on the port number. For example, to forward traffic from the Internet to a device on the private network with IP address 192.168.1.10 and port 80, you can use the following NAT rule:
nat (outside,inside) source static any NAT-POOL service tcp 80 80- Define a security rule that will allow the forwarded traffic to reach the destination device or service on the private network. This rule should specify the NAT pool as the source of the traffic and the private network as the destination. For example:
access-list NAT-ACL extended permit tcp NAT-POOL 192.168.1.0 255.255.255.0 eq 80
access-group NAT-ACL in interface outside- Save the configuration and apply the changes.
This is just a basic example of how to configure NAT Port Forwarding on a Cisco ASA. There are many other configuration options and considerations that may be relevant in a specific deployment, such as security levels, access lists, and NAT exclusions. It is recommended to refer to the Cisco ASA documentation and best practices for more information on configuring and securing a network with NAT Port Forwarding.