Upgrade Palo Alto HA Firewall Pair
In this article we shall learn to upgrade Palo Alto NGFW OS which are deployed in HA Pair. Below is the table of content so you can skip to specific step.
Table of contents
To avoid downtime when upgrading firewalls that are in a high availability (HA) configuration, update one HA peer at a time: For active/active firewalls, it doesn’t matter which peer you upgrade first (though for simplicity, this procedure shows you how to upgrade the active-secondary peer first.
To avoid impacting traffic, plan to upgrade within the outage window. Ensure the firewalls are connected to a reliable power source. A loss of power during an upgrade can make firewalls unusable.
For active/passive firewalls, you must upgrade the passive peer first, suspend the active peer (fail over), update the active peer, and then return that peer to a functional state (fail back). To prevent failover during the upgrade of the HA peers, you must make sure preemption is disabled before proceeding with the upgrade. You only need to disable preemption on one peer in the pair.
Step 1: Save Current Configuration:
Save a backup of the current configuration file. Perform this step on each firewall in HA pair.
| Although the firewall automatically creates a backup of the configuration, it is a best practice to create and externally store a backup before you upgrade. |
- To do so, Select Device > Setup > Operations and click Export named configuration snapshot.
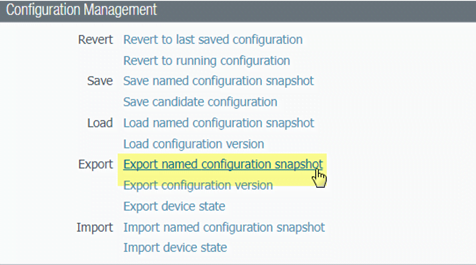
- Select the XML file that contains your running configuration (for example, running-config.xml) and click OK to export the configuration file.
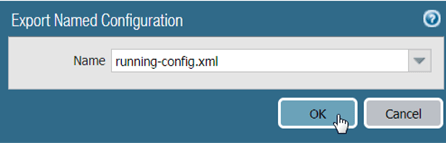
- Save the exported file to a location external to the firewall. You can use this backup to restore the configuration if you have problems with the upgrade.
Step 2: Verify User-ID Agent State
If you have enabled User-ID, after you upgrade, the firewall clears the current IP address-to-username and group mappings so that they can be repopulated with the attributes from the User-ID sources. To estimate the time required for your environment to repopulate the mappings, run the following CLI commands on the firewall.
- For IP address-to-username mappings:
- show user user-id-agent state all
- show user server-monitor state all
- For group mappings:
- show user server-monitor state all
Step 3: Ensure HA Pair Using Current OS Release
Ensure that each firewall in the HA pair is running the latest content release version.
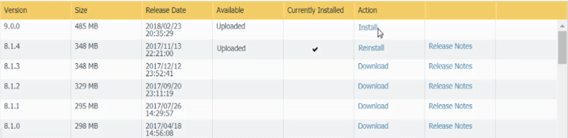
- Select Device > Dynamic Updates and check which Applications or Applications and Threats to determine which update is Currently Installed.
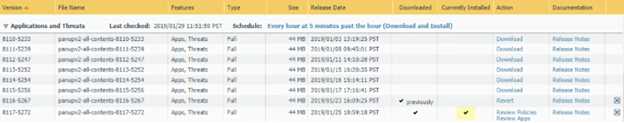
- Locate and Download the desired content release version. After you successfully download a content update file, the link in the Action column changes from Download to Install for that content release version.
- Install the update. You must install the update on both peers.
Recommended Reading
Step 4: Disable preemption on the first peer in each pair.
You only need to disable this setting on one firewall in the HA pair but ensure that the commit is successful before you proceed with the upgrade.
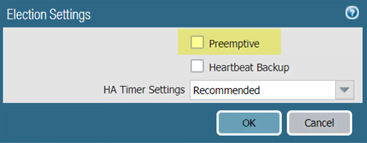
- Select Device > High Availability and edit the Election Settings.
- If enabled, disable (clear) the Preemptive setting and click OK.
- Commit the change.
Step 5: Install PAN-OS 9.1 on the first peer.
To minimize downtime in an active/passive configuration, upgrade the passive peer first. For an active/active configuration, upgrade the secondary peer first. As a best practice, if you are using an active/active configuration, we recommend upgrading both peers during the same maintenance window.
If you want to test that HA is functioning properly before the upgrade, consider upgrading the active peer in an active/passive configuration first to ensure that failover occurs without incident.
- On the first peer, select Device > Software and click Check Now for the latest updates.
- Locate and download PANOS 9.1.0
- After you download the image (or, for a manual upgrade, after you upload the image), Install the image.
- After the installation completes successfully, reboot using one of the following methods:
- If you are prompted to reboot, click Yes.
- If you are not prompted to reboot, select Device > Setup > Operations and Reboot Device.
- After the device finishes rebooting, view the High Availability widget on the Dashboard and verify that the device you just upgraded is still the passive or active-secondary peer in the HA configuration.
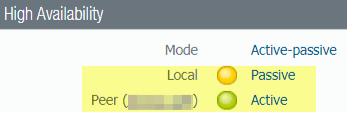
Step 6: Install PAN-OS 9.1 on the second peer
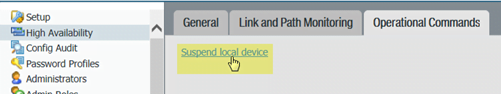
- (Active/passive configurations only) Suspend the active peer so that HA fails over to the peer you just upgraded.
- On the active peer, select Device > High Availability > Operational Commands and click Suspend local device.
- View the High Availability widget on the Dashboard and verify that the state changes to Passive.
- On the other peer, verify that it is active and is passing traffic (Monitor > Session Browser).
- On the second peer, select Device > Software and click Check Now for the latest updates.
- Locate and Download PAN-OS 9.1.0.
- After you download the image, Install it.
- After the installation completes successfully, reboot using one of the following methods:
- If you are prompted to reboot, click Yes.
- If you are not prompted to reboot, select Device > Setup > Operations and Reboot Device.
- (Active/passive configurations only) From the CLI of the peer you just upgraded, run the following command to make the firewall functional again:
request high-availability state functional
Step 7: Verify that both peers are passing traffic as expected.
In an active/passive configuration, only the active peer should be passing traffic; both peers should be passing traffic in an active/active configuration.
Run the following CLI commands to confirm that the upgrade succeeded:
- (Active peers only) To verify that active peers are passing traffic, run the “show session all” command.
- To verify session synchronization, run the “show high-availability interface ha2” command and make sure that the Hardware Interface counters on the CPU table are increasing as follows:
- In an active/active configuration, you will see packets received and packets transmitted on both peers.
Step 8: Enable Preemption:
If you disabled preemption prior to the upgrade, re-enable it now.
- Select Device > High Availability and edit the Election Settings.
- Select Preemptive and click OK.
- Commit the change.
In this article we have learnt to successfully upgrade Palo Alto OS which are deployed High Availability Clusters. I hope this has been informative for you and would like to thank you.

