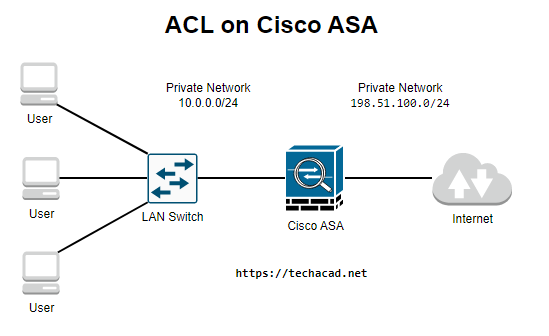
Introduction to Access Control List (ACL) on Cisco ASA
Cisco ASA access control lists ACL are used to control inbound and outbound traffic on a Cisco Adaptive Security Appliance (ASA). Access lists consist of a series of permit and deny statements that specify which traffic is allowed or denied based on various criteria such as source and destination IP addresses, protocols, and port numbers.
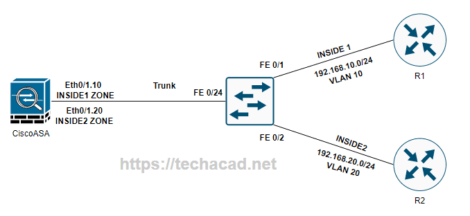
Access lists can be applied to various interfaces on the ASA, including the inside, outside, and DMZ interfaces. The inside interface represents the network behind the ASA, while the outside interface represents the network facing the Internet. The DMZ interface is a separate network segment that is typically used to host public servers such as web servers.
recommended reading
There are two types of access lists on the ASA: standard and extended. Standard access lists use a simple matching criteria based on the source IP address, while extended access lists use a more comprehensive matching criteria that can include the source and destination IP addresses, protocol, and port numbers.
Without any access-lists, the ASA will allow traffic from a higher security level to a lower security level. All other traffic is dropped. If you have no idea what security levels on the ASA are about then read this post first. Access-lists are created globally and then applied with the access-group command. They can be applied in- or outbound.
Here is an example of a standard access list that allows all traffic from the IP address 192.168.1.100:
access-list inside_access_in permit ip host 192.168.1.100 anyThis access list can be applied to the inside interface with the following command:
access-group inside_access_in in interface insideHere is an example of an extended access list that allows HTTP traffic from any source to a web server with the IP address 192.168.1.200 on the DMZ interface:
access-list dmz_access_in permit tcp any host 192.168.1.200 eq 80This access list can be applied to the DMZ interface with the following command:
access-group dmz_access_in in interface dmzIt’s important to note that access lists are evaluated in order, and the first matching rule is applied. Therefore, it’s important to place more specific rules before less specific ones. For example, if you have a rule that allows all traffic from any source and a later rule that denies traffic from a specific IP address, the second rule will never be applied because the first rule will always match first.
recommended reading
In summary, Cisco ASA access lists are a powerful tool for controlling inbound and outbound traffic on the ASA and can be used to secure networks and protect against malicious traffic.